2016
Secure Software Distribution in an Adversarial World

MTLS in a Microservices World

Orchestrating Least Privilege

Duo Tech Talks: Secure Software Distribution in an Adversarial World

2015
Green Font, Black Background – Docker Security By Example
Web Summit 2015: Cloud, Open-Source, Security

A Docker Image Walks Into A Notary

From 0 To 0xdeadbeef - Security Mistakes That Will Haunt Your Startup

Forbes: Apple's HomeKit Security Too Demanding

An IDS For Browser Hijacking
Least Privilege Microservices

NY Times: Keeping Your Car Safe From Electronic Thieves

The Register UK: Docker Hires'n'acquires To Cure Its Security Headaches

2014
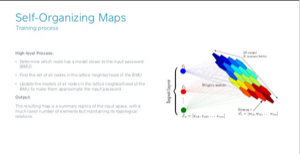
Local Password Validation Using Self-Organizing Maps
Human Botnet: Scaling Your Security Organization

Crypto-Anchoring: Defending Against Offline Attacks
Multipath TCP: The Path To Multipath
2013
Leveraging Honest Users: Stealth Command-And-Control Of Botnets

ArsTecnica: Engineer Can’t Get Decent Dinner Reservations

Bletchley: Dealing With HSMs So You Don't Have To
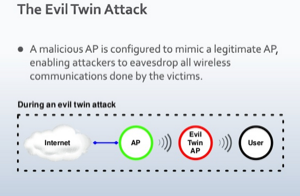
WiFiHop - Mitigating The Evil Twin Attack Through Multi-Hop Detection
Observable Non-Sybil Quorums Construction In One-Hop Wireless Ad Hoc Networks
On The Use Of Radio Resource Tests In Wireless Ad Hoc Networks